Compliance
Compliance (regulatory compliance) means conforming to comply with relevant laws and regulations. Together with KYC Spider in Zug Eurospider has in-depth compliance know-how.
In the past year (2024), the Swiss Federal Court issued several rulings on money laundering and financial offenses, emphasizing important aspects of the due diligence obligations of banks and financial intermediaries.
At the 11th member event of the Open Banking Project, our IT specialist Adriano Meyer presented the current trends in the KYC sector. He gave an interesting presentation on the digital onboarding of customers.
“You have to be adaptable and open to adjustments”, said Simonetta Sommaruga, President of the Swiss Confederation, on August 12, 2020 at the press conference held by the Federal Council [1]. This not only applies to combating the COVID-19 pandemic, but also to combating money laundering. We’ve identified a few issues with the false report about an alleged coronavirus death [2] which are also relevant for compliance.
Some time ago, we posted an expert article about compliance and game theory. Several readers may have wondered what compliance has to do with gaming. Game theory belongs to the realm of mathematics and economics. The term is a misnomer because modern game theory does not focus on board games and the like. “Strategic interaction theory” or “strategic conflict theory” would be more accurate descriptions.
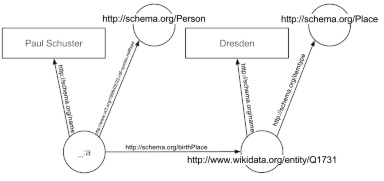
The term “Semantic Web” was coined by Tim Berners-Lee, the inventor of the World Wide Web. His idea was to create a “web of data” that could be interpreted by machines – a goal that is also highly relevant the area of compliance. What is known as the Resource Description Framework (RDF) is used to achieve this goal. RDF enables automated inferencing, which is also beneficial for compliance purposes.
Complete Revision of the Federal Data Protection Act
Complete Revision of the Federal Data Protection Act: „As of 15th September 2017, draft and report for a completely revised Federal Data Protection Act is public. In a first step parliament and the people agreed to adaptations in order to be compliant with EU law. The second part of the revision is debated by the parliament since September 2019. Data Protection is to be increased by giving people more control over their private data as well as reinforcing transparency regarding the handling of confidential data.”
Links: datenrecht.ch